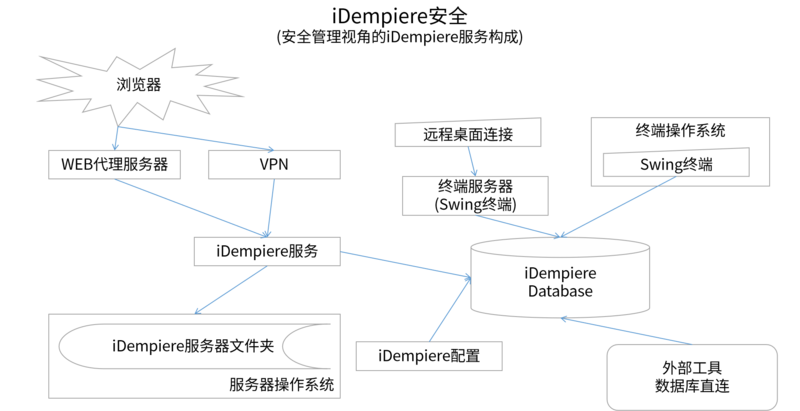
IDempiere服务器安全
英文原文: iDempiere服务器安全
原始贡献者: Carlos Ruiz - GlobalQSS - 请各位随时改进该文章。
2015全球会议的谈话
在 2015年iDempiere全球会议 期间,Carlos做了一个关于安全的演讲,可以在Youtube上观看该演讲视频。
https://www.youtube.com/watch?v=mhjA1B4PHFs
初始化步骤
请参看下述步骤的详细说明:
- 在系统配置(SysConfig)中配置 ZK_ROOT_FOLDER_BROWSER
- 更改加密秘钥
- 散列密码 (如果没有使用散列密码,需要加密 AD_User.Password 和 AD_Password_History.Password列)
- 加密数据库中包含密码的所有列 (如果已经使用了散列密码则不需要加密AD_User.Password 和AD_Password_History.Password列)
- 设置密码规则
- 更改用户SuperUser, System, GardenAdmin, GardenUser和WebService的缺省密码 仅iDChina:建议更改SuperUser, System, GardenAdmin, GardenUser和WebService的用户名称
- 创建新租户后更改默认密码 (在初始租户设置中,可以选择默认情况下不分配密码以提高安全性)
浏览器(chrome, firefox, safari, ie, opera)
https
请不要使用http,必须始终使用SSL加密的https
iDempiere已经不允许使用http,从浏览器访问时必须使用https。
如果使用了Nginx的话,请参看通过Nginx进行iDempiere的反向代理(英文)添加配置proxy_set_header X-Forwarded-Proto $scheme;
客户端证书
可以通过向用户提供客户端证书的方式来限制可以连接的用户
代理WEB服务器 (nginx, apache)
通过设置一台代理web服务器来公开用户所需的服务,大多数情况下仅公开webui即可
设置代理的推荐方法
Nginx:请查看通过Nginx进行iDempiere的反向代理(英文)
Apache:请查看GoogleGroups中的沟通信息
VPN (openvpn, cisco)
一些公司配置成进可以通过使用VPN访问iDempiere,这样会更加安全。在这个场景下可以不关心DNS或者Nginx配置。
iDempiere相关的WEB服务
zkwebui
这是用户需要访问的UI前端,所以可以配置代理、发布。
idempiereMonitor
该服务用于管理员对iDempiere进行管理和监控,需要将其隐藏起来,严格控制访问权限(配置成通过代理或仅允许通过VPN访问),不能让一般用户访问。
felix console
该服务用于管理员对iDempiere插件进行管理,需要将其隐藏起来,严格控制访问权限(配置成通过代理或仅允许通过VPN访问),不能让一般用户访问。
REST Web服务
我们有一个被广泛使用的REST插件 widely used REST plugin ),通过该插件可以在iDempiere上启用REST WEB服务。由于该插件功能过于强大,不建议公开。 REST Web服务的使用取决于角色和用户配置,它可以执行特别的查询和CRUD操作、可以访问所有的表。
如果需要公开REST WEB服务的话,推荐使用API网关公开。WIKI中提供了如下事例:
Proxy iDempiere-Rest Through KrakenD
cxf webservices
如果您计划公开SOAP/XML Web服务层,建议仔细配置其安全层,查看Web服务安全性以了解更多信息。
已弃用的REST WEB服务
在7.1之后以及删除了会返回数据库密码的Web服务
webstore
iDempiere通过一个外部插件来提供网店功能,可以在下述地址获取
https://github.com/idempiere/idempiere-webstore
该插件使用的技术比较陈旧并未经维护,如果需要在生产中公开它的话,请严格仔细审查对安全的影响。
fitnesse
一个用于进行测试的外部插件,该插件提供了Web服务,可以在下述地址获取
https://github.com/idempiere/idempiere-fitnesse
该插件仅可以在测试环境使用,不可以在生产环境提供。
其他外部扩展 (手机端等)
还有一些第三方插件提供WEB服务,例如ADAXA_Mobile(已弃用)或者BX Service Vaadin Mobile。
与每一个外部插件一样,请严格仔细审查对安全的影响后使用。
服务器操作系统 (linux, windows, mac)
Linux
NEVER install iDempiere with root, this is a common advice for any software that exposes services to the internet. If somebody - for any reason - could exploit iDempiere to gain access to the operating system, they'll have the permissions from the user that runs iDempiere, so if you run it with root, they'll have complete access to the server. For the same reason it is recommended that you consider carefully which permissions and access to give to the operating system user that is running iDempiere.
Windows
Many developers use iDempiere in Windows for development, but very few people run iDempiere in production using Windows, some of the support scripts (f.e. applying migration scripts) are just developed for Linux, so you would need to do some tasks manually.
Linux is the preferred option.
openssl生成客户端证书
nginx, apache can be configured to allow access to clients that are authenticated with a client certificate
idempiere-server文件夹
必须保护文件idempiereEnv.properties、idempiele.propertie、.idpass以及包含数据库密码的其他一些文件。
- Windows:默认情况下,通常每个人都具有读取权限
- Linux:默认情况下文件受到保护,密码使用base64进行模糊处理
- There is a provision to customize the way to obfuscate/encrypt the password, or externalize it (avoid to save it on the server). Note externalizing the password protect against physical access (like stolen hard drive), but these passwords CANNOT be protected against a hacker accessing the live server, unless you sacrifice the ability to automate many things requiring manual intervention from an operator to provide some credentials.
swing client
swing客户端不安全,不推荐使用
database password encrypted in properties file
The database password on swing client is "encrypted" in a properties file, the problem is that the encryption algorithm is usually common and easy to decrypt, and even if you change it can be easily extracted from the jar files. There is the possibility of implementing alternative keys, algorithm or even classes to encrypt better the strings.
terminal server approach (nx, citrix, ts)
if definitely you are needing to use swing client is better to use it via a terminal server where you have control of the machines
jasper reports
- Be careful, jasper can read anything over the database, just install trusted reports.
- Consider including in your jasper queries the security layer of iDempiere, like is included by MRole.addAccessSQL, like:
- Restrict to the organizations the user has access to
- Take into account AD_Private_Access and AD_Record_Access
external tools
If you need to give direct SQL access to other tools like jasper, odbc/jdbc connections to libreoffice, datawarehouses, ETL, talend, etc - better consider creating a read-only user with access to preconfigured views. The views can contain the security filter for AD_Client_ID
database
iDempiere supports postgresql and oracle. Most implementations run on postgresql, however oracle support is good and permanently maintained.
dba user
By default the installers create a database user (usually named adempiere) with complete DBA/SUPERUSER permissions, this is, this user have ability to do everything on your database. It is possible to install iDempiere with a less powerful user, but you need to configure it manually
iDempiere configuration
New Tenant
When creating a new tenant, by default iDempiere assign a weak password which is the same as the user name. It is recommended better to disable the flag "Set Initial Password" and assign secure passwords to the new users manually after the tenant is created.
roles
- it is recommended to configure the security using access, not menus (menus don't restrict access - user still can zoom)
org access
You can configure organization access in the role window.
You can configure specific menus for roles, however it is important to note that the menu is just visual, the users can still navigate to the windows they have permissions using the zoom function.
db access (table, column)
You can configure / restrict access for roles using the Role Data Access window
private record & record access
To configure record access you must use the "Lock" button on the toolbar. This button can make a record:
- private: just visible for the user who locked it and the roles allowed to see locked records
- restricted: just visible for certain roles
NOTE ON ADVANCED ROLES
The advanced roles are intended for IT on tenant side - do not give an advanced role to an end user. You must consider advanced roles as SuperUser, they have access to all security holes.
Also you must consider SuperUser as if it has access to the operating system user used to install iDempiere on the server.
In other words, the advanced roles have access to iDempiere features that can be easily exploited to gain access to SuperUser in the application, to the database as a DBA, and to the operating system as the user that run iDempiere server.
users
iDempiere comes with 5 users by default with very easy and insecure passwords. It is a mandatory first step to change these passwords on: SuperUser, System, GardenAdmin, GardenUser, WebService
sensitive fields (like passwords)
It is recommended to encrypt sensitive data, iDempiere has a mechanism to encrypt that can be easily enabled/disabled per column.
encryption
To encrypt data in the database, iDempiere uses an algorithm and a key that is exposed in the open source code. So, is not very secure.
In order to encrypt sensitive data - as recommended - it is better to configure a proper keystore, this can be achieved setting idempiere.ks and idempiere-ks.properties in the server. As of today, there is no documentation about how to use this feature, check the class DefaultKeyStore for more defaults about the implementation.
hashed passwords
It is absolutely recommended as one of the first steps of your installation to use the hashed passwords feature, you can find more information at NF1.0 HashedPasswords. These passwords are very secure as they are not encrypted, but hashed, so it can be seen as a one-way encryption, for example even if somebody obtain the hashed passwords with direct access to the database, they cannot go back and figure out the password.
password rules
It is recommended to setup a set of password rules for your users. You can find more information at NF1.0 PasswordRules
user locking
iDempiere provides features to manage automatic user locking on certain events. It is recommended to setup these features. You can find more information at NF1.0 User_Locking
ZK_ROOT_FOLDER_BROWSER
The SysConfig key ZK_ROOT_FOLDER_BROWSER defines the folder that is shown when clicking on a Folder type field.
As this folder can be exploited to get information from the server, it is recommended to set this SysConfig key to a secure folder in your server that does not contain any sensitive information.
Multi-factor Authentication
Since version 8.2.2021-06-09 iDempiere is able to manage Multi-factor Authentication on login time. Refer to Configure MFA for details about how to setup and use this feature.
You can trace MFA failures in the file AuthFailure.log, it is recommended to setup a mechanism to inform users when MFA failures happen, it can mean that their password was leaked.
tracing possible attacks
Every trial to login with a wrong password, or an MFA failure is recorded in the file AuthFailure.log
external tools to deny service on attacks
You can use tools like denyhosts to ban IP addresses that are testing passwords based on the AuthFailure.log file